- No. API Calls
- 549
- Uploaded
- Aug 31, 2024
- Base Model
- cogvideox
- Model ID
- cogvideox
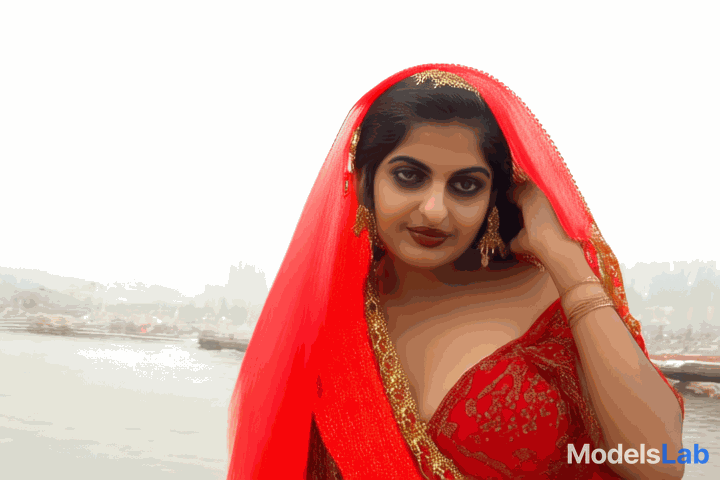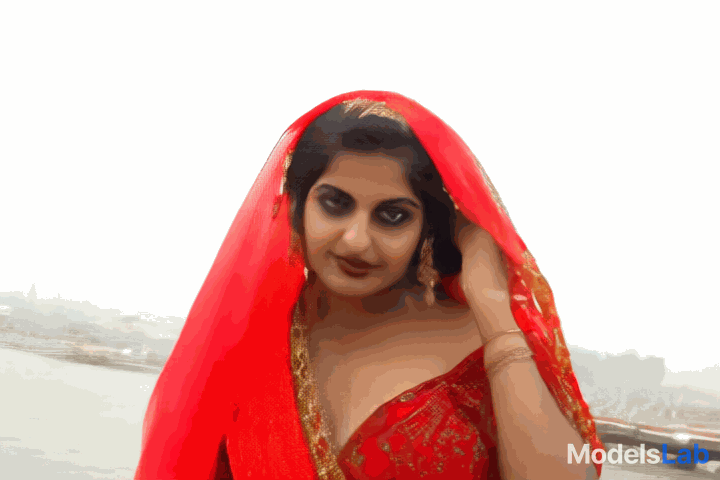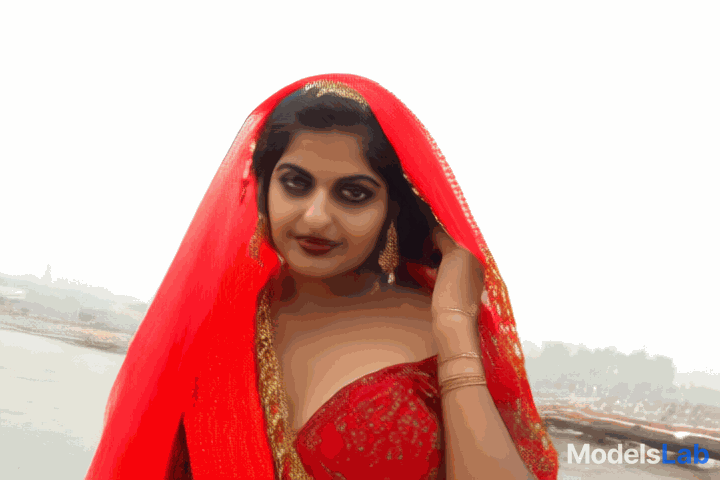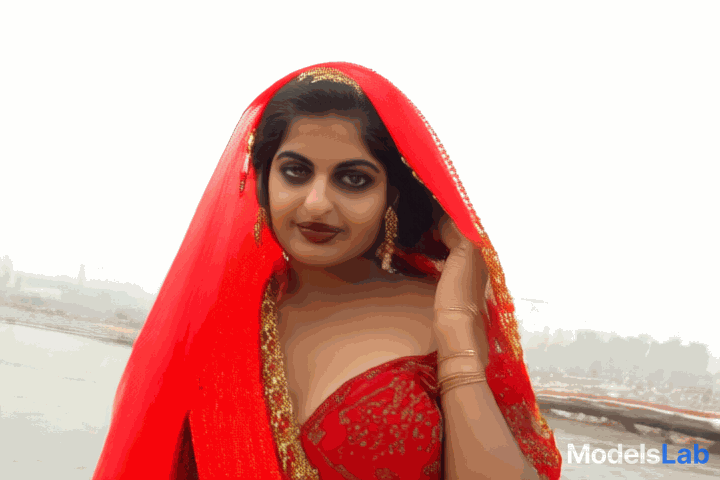
Video
Generated
Video generated with cogvideox and its prompt

Erstelle ein Video über das sternzeichen Jungfrau mit 10 Fakten für TIKTOK. Einleitung soll sein 10 unglaubliche Fakten über das sternzeichen Jungfrau. Jeder Fakt soll einzeln angezeigt werden und kurz erläutert werden

In a dimly lit room with an eerie glow emanating from multiple computer monitors, a cybercriminal sits hunched over a mechanical keyboard. The criminal is clad in dark, nondescript clothing, with a hoodie pulled up, casting shadows over their face, obscuring their identity. Only the reflection of the screen's light flickers across their eyes, filled with focus and intent. Their fingers move rapidly, dancing across the keys with precision, each keystroke loud and deliberate, as though they've done this a thousand times. The desk is cluttered with scattered devices—external drives, phones, and cables—hinting at a deeper, more complex operation. The mechanical clack of the keyboard resonates in the room, punctuated occasionally by the faint hum of cooling fans from the computer tower under the desk. Behind the criminal, one of the monitors displays a dynamic series of code lines scrolling down in rapid succession. Bright green and white letters flash against a pitch-black background, reminiscent of classic hacking visualizations. Each new line of code reflects a command or an infiltration attempt, steadily flowing down as the operation unfolds.

Girl smiling and sitting on bench, ultra HD video.

In a dimly lit room with an eerie glow emanating from multiple computer monitors, a cybercriminal sits hunched over a mechanical keyboard. The criminal is clad in dark, nondescript clothing, with a hoodie pulled up, casting shadows over their face, obscuring their identity. Only the reflection of the screen's light flickers across their eyes, filled with focus and intent. Their fingers move rapidly, dancing across the keys with precision, each keystroke loud and deliberate, as though they've done this a thousand times. The desk is cluttered with scattered devices—external drives, phones, and cables—hinting at a deeper, more complex operation. The mechanical clack of the keyboard resonates in the room, punctuated occasionally by the faint hum of cooling fans from the computer tower under the desk. Behind the criminal, one of the monitors displays a dynamic series of code lines scrolling down in rapid succession. Bright green and white letters flash against a pitch-black background, reminiscent of classic hacking visualizations. Each new line of code reflects a command or an infiltration attempt, steadily flowing down as the operation unfolds. On another monitor, a sophisticated graphical interface shows a network map, with nodes representing different servers, devices, and users. Some of the nodes are highlighted in red, indicating that they've been compromised, while others flash amber, signaling they're currently being breached. Digital pathways, represented by faint lines, connect the nodes, illuminating as the hacker gains unauthorized access to additional systems. A third screen shows a command terminal, where the hacker has launched an attack. Cryptic commands and strings of code scroll down, executing one after another. The words 'BRUTE FORCE ATTACK,' 'EXPLOIT,' and 'BYTES EXFILTRATED' flash briefly on the terminal, followed by percentages denoting the success of the malicious activity. Files are being copied in the background, their progress bars inching forward toward completion. As the hacker continues typing, an alert pops up on one of the monitors: 'Access Granted.' The criminal smirks ever so slightly, their hands never stopping as they push deeper into the system. The screens now begin to show activity logs from the compromised server—details about the network, usernames, encrypted passwords—all flowing into the hacker’s system. The final monitor lights up with a visual representation of a data extraction process, with lines connecting from the target server to the hacker’s own system. Gigabytes of sensitive information are being siphoned off in real time, the screen displaying file names: 'Confidential_Report.pdf,' 'Financials_2024.xlsx,' 'Employee_Database.sql.' In the background, security software tries to fight back, but it’s too late—the system's defenses are overwhelmed. A small notification appears in the corner of the screen, stating: 'Firewall Bypassed, Encryption Disabled.' Suddenly, a live feed of the server room appears on the screen, displaying security camera footage of a sterile, high-tech facility. The hacker has even infiltrated the building's CCTV system. The criminal's fingers slow, as they monitor the final steps of the data breach. The operation is almost complete. In the faint glow of the screens, the entire scene reeks of anonymity and calculated chaos. The criminal blends perfectly into the shadows, orchestrating a silent but devastating heist—one keypress at a time.

In a dimly lit room with an eerie glow emanating from multiple computer monitors, a cybercriminal sits hunched over a mechanical keyboard. The criminal is clad in dark, nondescript clothing, with a hoodie pulled up, casting shadows over their face, obscuring their identity. Only the reflection of the screen's light flickers across their eyes, filled with focus and intent. Their fingers move rapidly, dancing across the keys with precision, each keystroke loud and deliberate, as though they've done this a thousand times. The desk is cluttered with scattered devices—external drives, phones, and cables—hinting at a deeper, more complex operation. The mechanical clack of the keyboard resonates in the room, punctuated occasionally by the faint hum of cooling fans from the computer tower under the desk. Behind the criminal, one of the monitors displays a dynamic series of code lines scrolling down in rapid succession. Bright green and white letters flash against a pitch-black background, reminiscent of classic hacking visualizations. Each new line of code reflects a command or an infiltration attempt, steadily flowing down as the operation unfolds. On another monitor, a sophisticated graphical interface shows a network map, with nodes representing different servers, devices, and users. Some of the nodes are highlighted in red, indicating that they've been compromised, while others flash amber, signaling they're currently being breached. Digital pathways, represented by faint lines, connect the nodes, illuminating as the hacker gains unauthorized access to additional systems. A third screen shows a command terminal, where the hacker has launched an attack. Cryptic commands and strings of code scroll down, executing one after another. The words 'BRUTE FORCE ATTACK,' 'EXPLOIT,' and 'BYTES EXFILTRATED' flash briefly on the terminal, followed by percentages denoting the success of the malicious activity. Files are being copied in the background, their progress bars inching forward toward completion. As the hacker continues typing, an alert pops up on one of the monitors: 'Access Granted.' The criminal smirks ever so slightly, their hands never stopping as they push deeper into the system. The screens now begin to show activity logs from the compromised server—details about the network, usernames, encrypted passwords—all flowing into the hacker’s system. The final monitor lights up with a visual representation of a data extraction process, with lines connecting from the target server to the hacker’s own system. Gigabytes of sensitive information are being siphoned off in real time, the screen displaying file names: 'Confidential_Report.pdf,' 'Financials_2024.xlsx,' 'Employee_Database.sql.' In the background, security software tries to fight back, but it’s too late—the system's defenses are overwhelmed. A small notification appears in the corner of the screen, stating: 'Firewall Bypassed, Encryption Disabled.' Suddenly, a live feed of the server room appears on the screen, displaying security camera footage of a sterile, high-tech facility. The hacker has even infiltrated the building's CCTV system. The criminal's fingers slow, as they monitor the final steps of the data breach. The operation is almost complete. In the faint glow of the screens, the entire scene reeks of anonymity and calculated chaos. The criminal blends perfectly into the shadows, orchestrating a silent but devastating heist—one keypress at a time.

Create an video of Donald Trump being elected President because tons of BTC-loving Crypto Bros living in their parents' basement turned out to vote for Trump because of his pro-BTC policies.

Erstelle ein Video über das sternzeichen Jungfrau mit 10 Fakten für TIKTOK. Einleitung soll sein 10 unglaubliche Fakten über das sternzeichen Jungfrau. Jeder Fakt soll einzeln angezeigt werden und kurz erläutert werden

a cyber criminal typing on his keyboard, then, a screen shows a hacking activity taking in place